Security is essential for every organization, that’s why Automat-IT pays great attention to it during project delivery and well-architected review. AWS has several really impressive security related services that help us build a safe infrastructure and continuously monitor compliance. In the previous post we demonstrated how to enable AWS Security Hub for a multi-account AWS environment. We suggest our customers enable AWS Security Hub along with given integrations, like GuardDuty, Inspector, Macie, Detective, IAM Access Analyzer, Audit Manager and Chatbot, which will be described in this post.
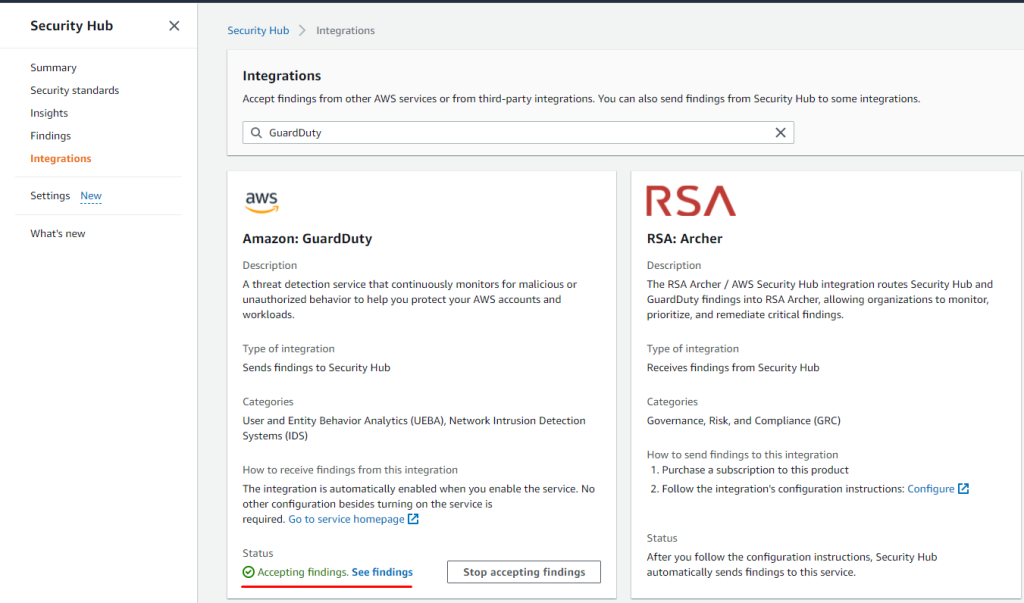
Amazon GuardDuty integration
Automat-IT enables Amazon GuardDuty by default in every project since the service was released. We described how we deploy this thread detection system in a multi-account AWS environment in the previous post. Here we will look at GuardDuty integration into AWS Security Hub.
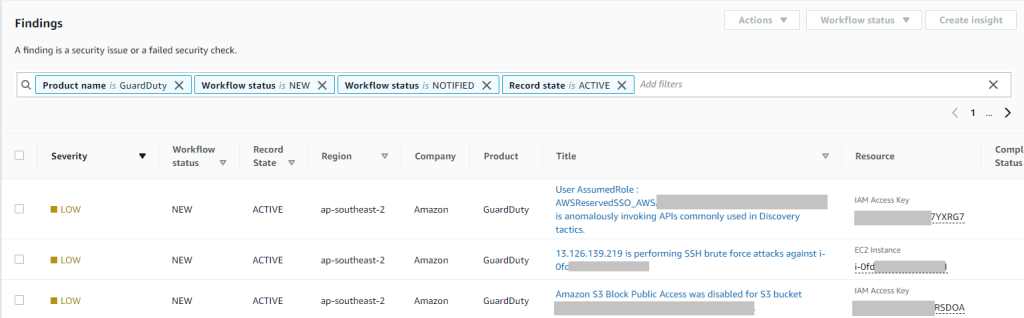
Once you enable Amazon GuardDuty and AWS Security Hub, findings are automatically delivered to the Security Hub console.
Amazon GuardDuty findings from all accounts within AWS Organizations are displayed in the AWS Security Hub console in the central Audic account.
Amazon Macie integration
Amazon Macie is a fully managed data security and data privacy service that uses machine learning and pattern matching to discover and protect your sensitive data in AWS. Macie automatically provides an inventory of Amazon S3 buckets including a list of unencrypted buckets, publicly accessible buckets, and buckets shared with AWS accounts outside those you have defined in AWS Organizations. Then, Macie applies machine learning and pattern matching techniques to the buckets you select to identify and alert you to sensitive data, such as personally identifiable information (PII).
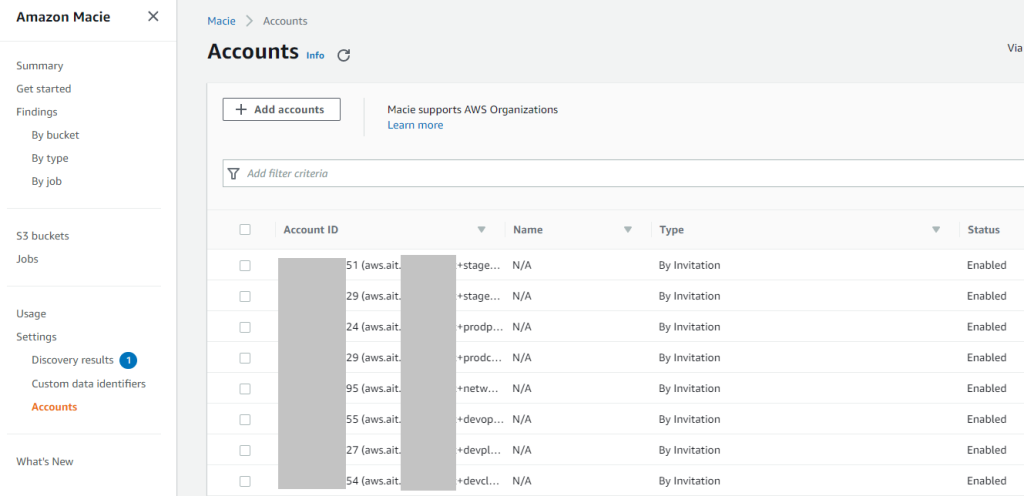
Amazon Macie allows the centralized account as we have in GuardDuty. Audit account is central for Amazon Macie and member accounts are invited to join.
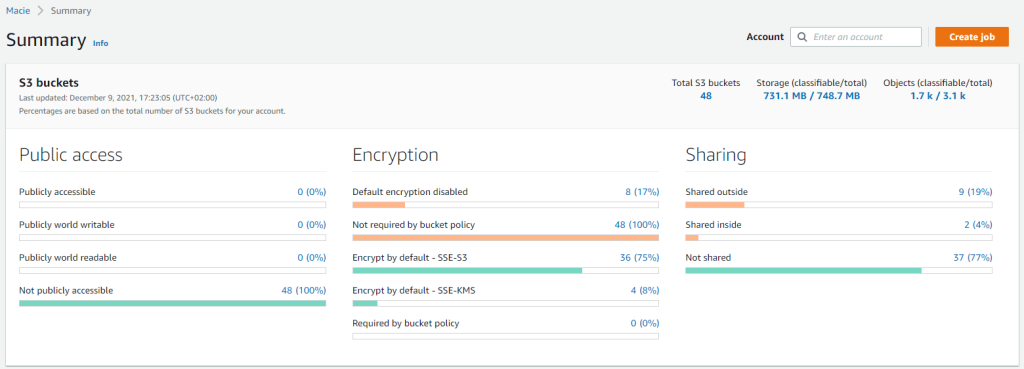
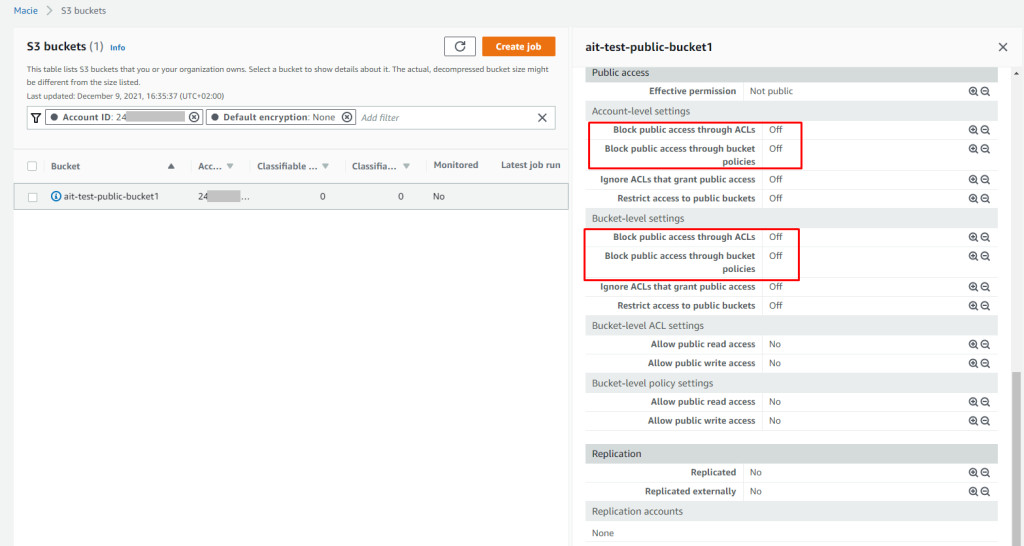
Summary shows overall status for S3 service including public access and encryption configuration.
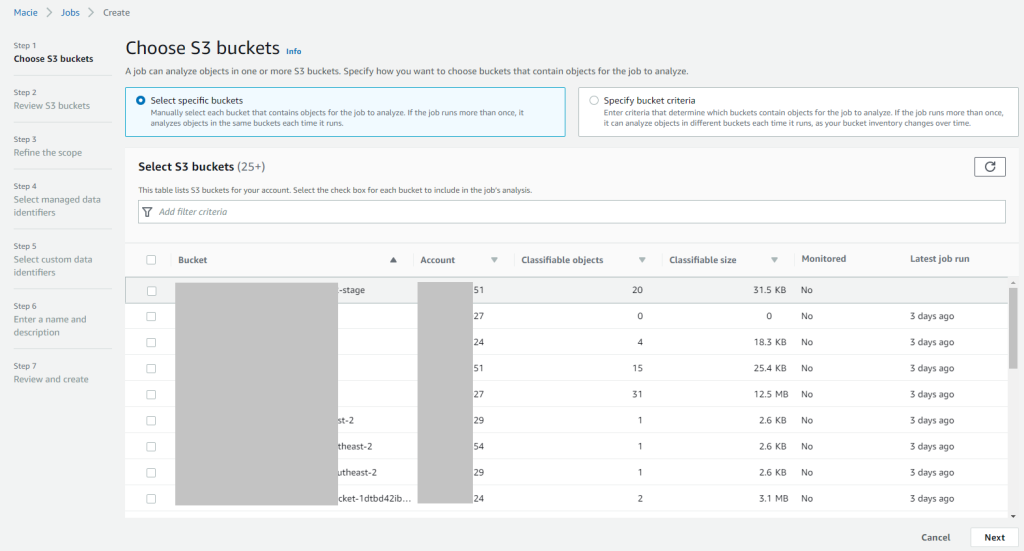
Moreover Amazon Macie allows to run Scheduled or One-time jobs and scan objects for sensitive data in selected buckets.
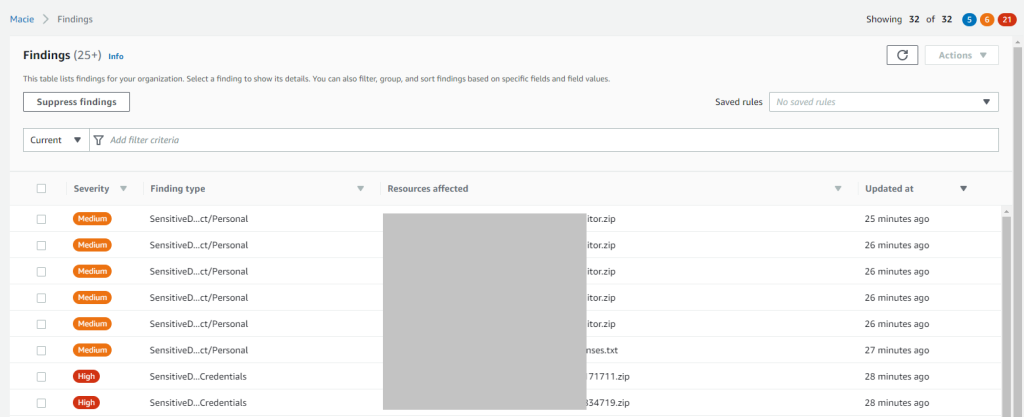
In the following example the scanning job has found several issued, including personal data and credentials in txt files and zip archives:
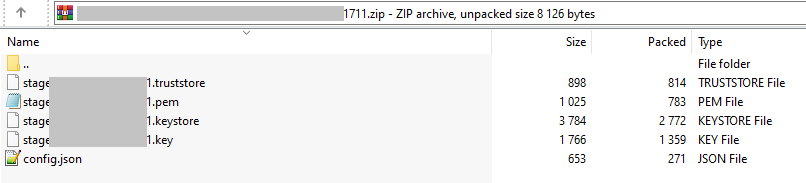
When we downloaded the mentioned zip archive with a finding “Credentials”, we saw a private key inside.
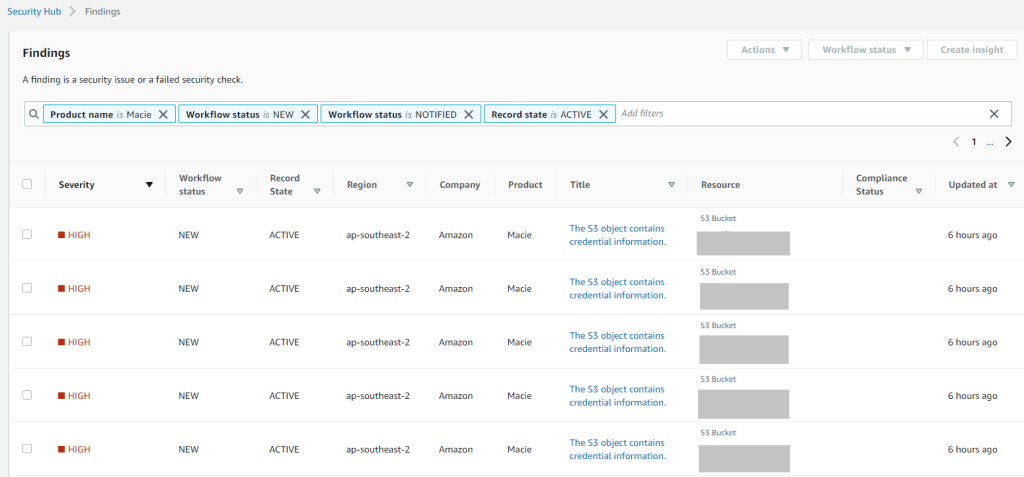
Once you enable Amazon Macie and AWS Security Hub, findings are automatically delivered to the Security Hub console.
Amazon Macie findings from all accounts within AWS Organizations are displayed in the AWS Security Hub console in the central Audic account.
You can quickly get started with Macie leveraging the 30-day free trial. By enabling the service, only the S3 bucket inventory and bucket-level evaluation charges apply and those come at no-cost for the first 30 days. After the first 30 days, the bucket evaluation will cost $0.10 per S3 bucket. First 1 GB / month of data processing is free, next 50,000 GB / month – $1.00 per GB.
IAM Access Analyzer integration
AWS IAM Access Analyzer helps you identify the resources in your organization and accounts, such as Amazon S3 buckets or IAM roles, shared with an external entity. This lets you identify unintended access to your resources and data, which is a security risk. An external entity can be another AWS account, a root user, an IAM user or role, a federated user, an AWS service, an anonymous user, or other entity that you can use to create a filter.
Despite having IAM in the name, IAM Access Analyzer is a regional service. It analyzes only policies applied to resources in the same AWS Region where it’s enabled. To monitor all resources in your AWS environment, you must create an analyzer to enable Access Analyzer in each Region where you’re using supported AWS resources.
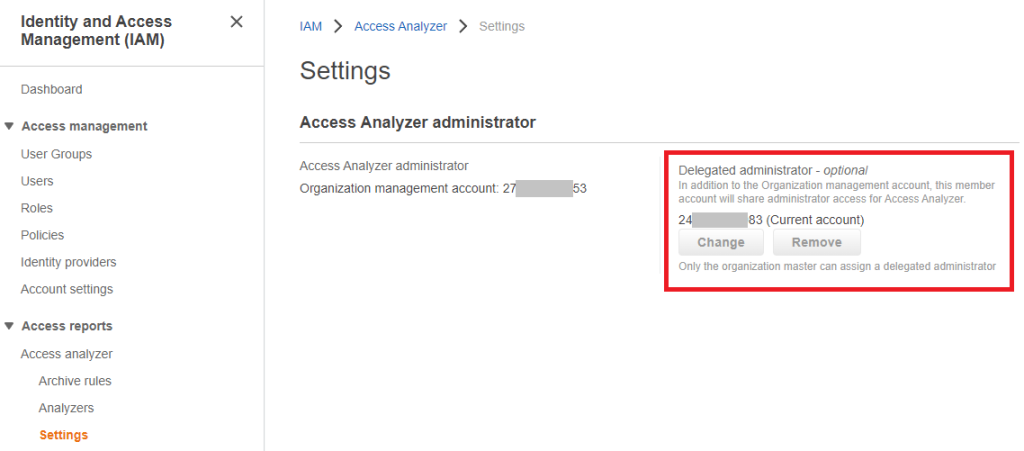
By default the AWS organization master account is administrator for IAM Access Analyzer in a multi-account environment, but you can delegate an administration (it’s again will be the Audit account).
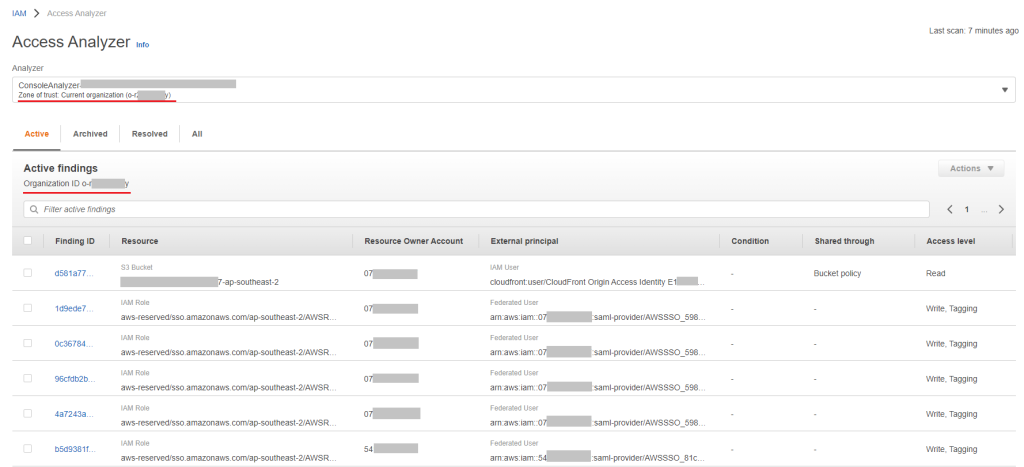
We can create an analyzer for the current AWS account or for the whole AWS organization, as in the following example:
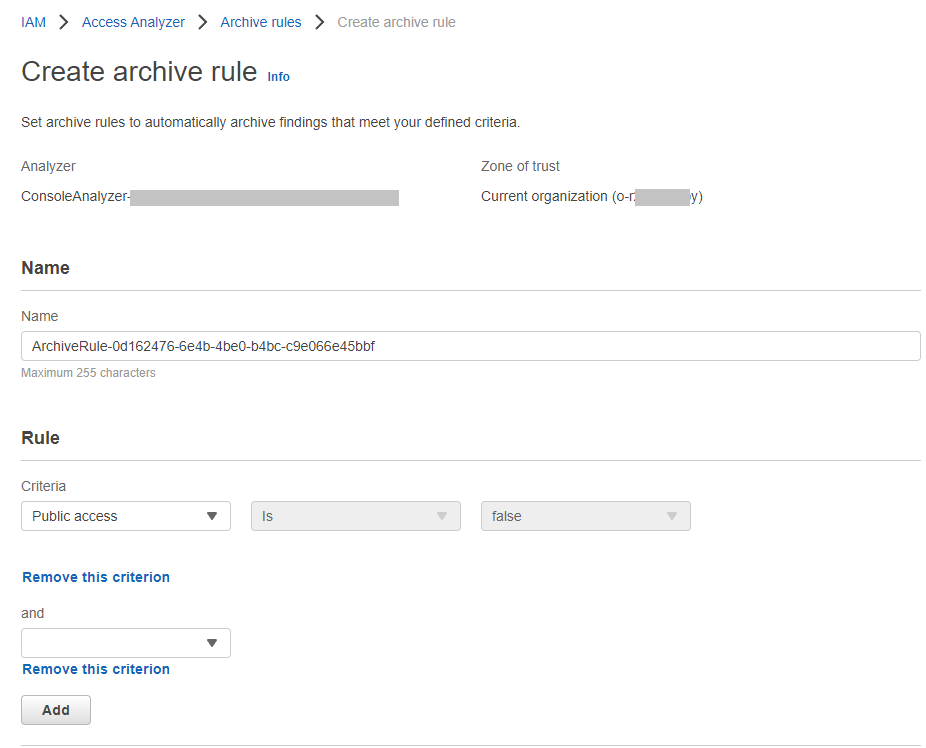
If some findings are not relevant, you can configure an archive rule with different conditions that will automatically archive findings, for example we have the finding above that shows that an external principal Cloudfront (with an origin access identity) accesses S3 bucket. We know that it is intended access and expected for us, so we don’t need such notification.
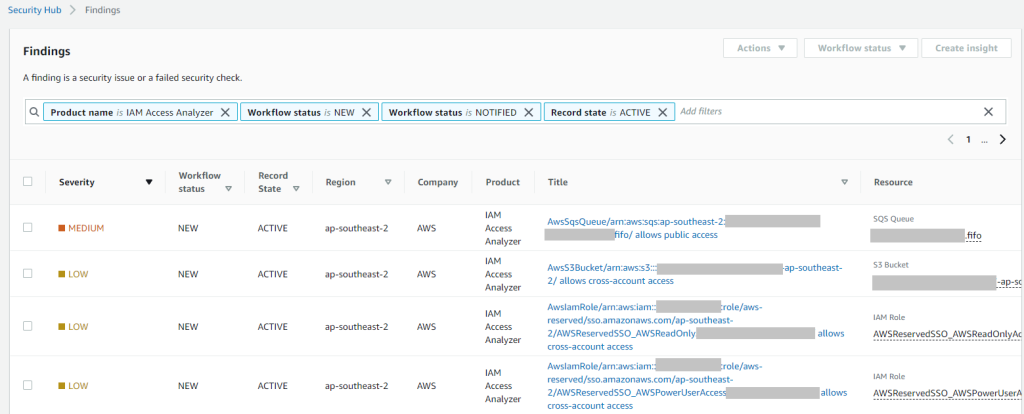
Once you enable IAM Access Analyser and AWS Security Hub, findings are automatically delivered to the Security Hub console.
IAM Access Analyzer policy validation is available at no additional cost in all commercial AWS Regions, AWS China regions, and AWS GovCloud (US).
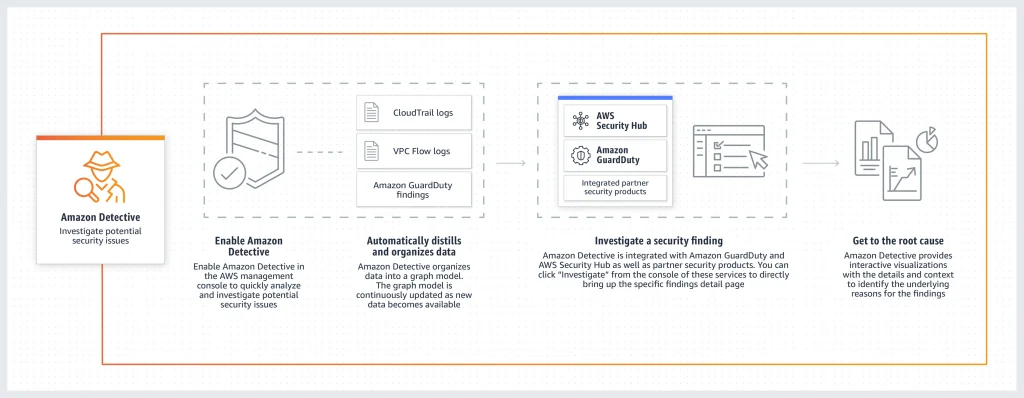
Amazon Detective integration
Amazon Detective makes it easy to analyze, investigate, and quickly identify the root cause of potential security issues or suspicious activities. Amazon Detective automatically collects log data from your AWS resources and uses machine learning, statistical analysis, and graph theory to build a linked set of data that enables you to easily conduct faster and more efficient security investigations.
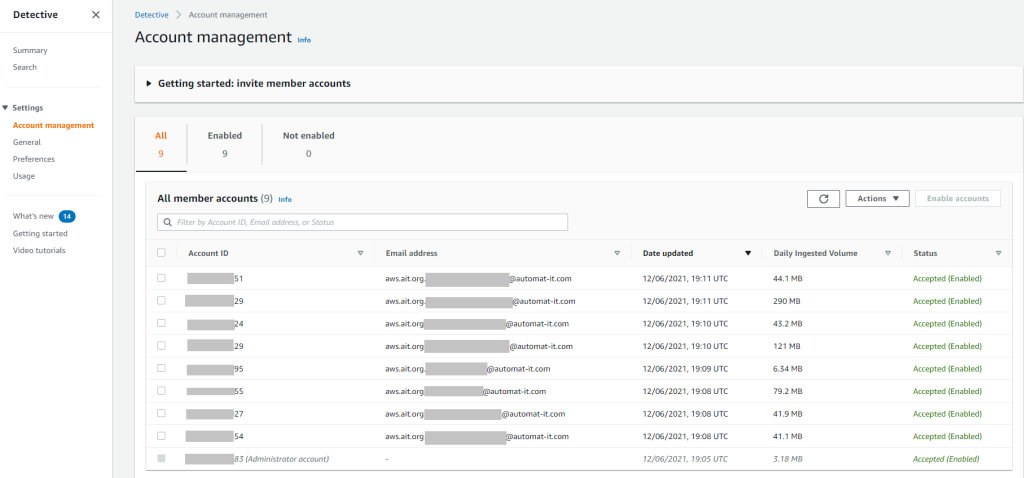
As other above mentioned AWS security services, Amazon Detective can be configured in a centralized manner. The “Audit” AWS account is an administrator that invites other accounts.
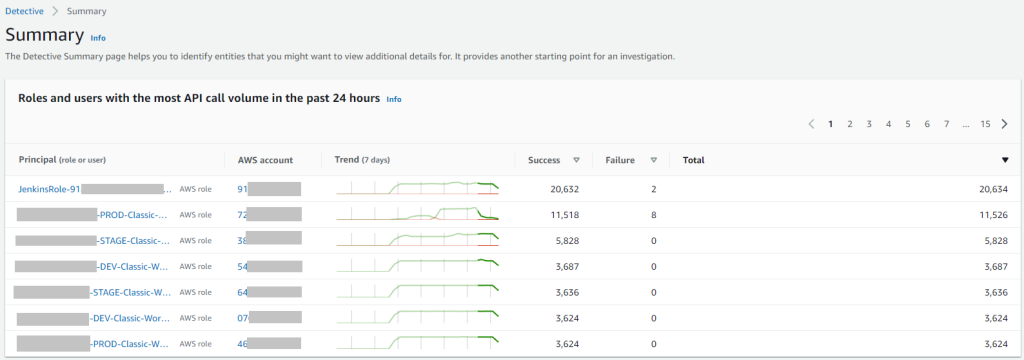
In the Amazon Detective summary we have three tabs. The first on is “Roles and users with the most API call volume in the past 24 hours”
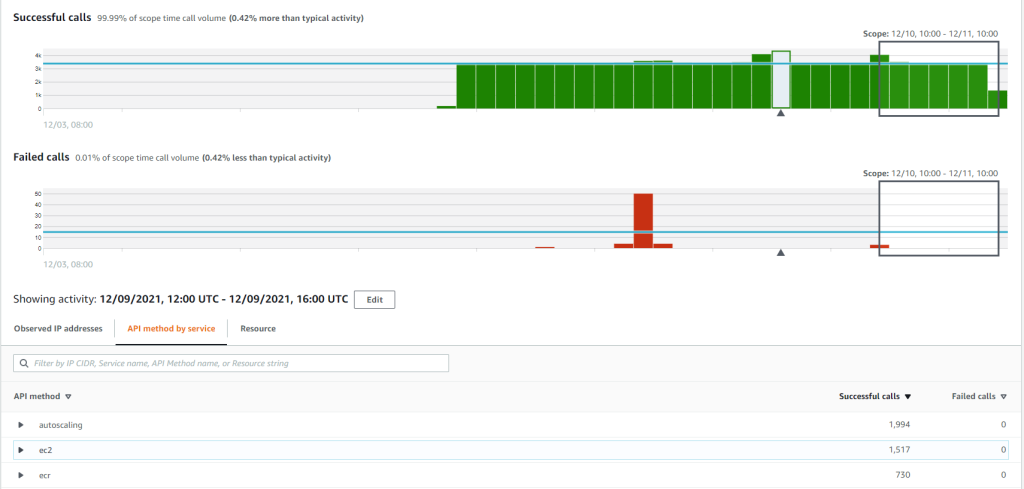
If you click to any principal, you will see details including success/fail rate, observer IP addresses, API method by service and called resources. This is useful for incident investigation and threat hunting.
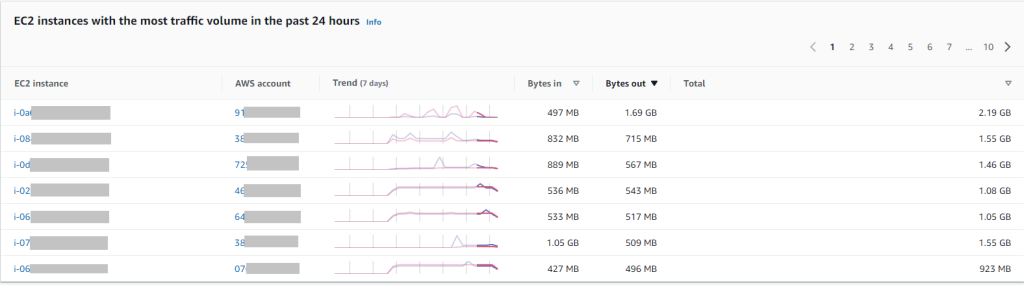
The second summary tab is “EC2 instances with the most traffic volume in the past 24 hours”. Here you can check if some spike in traffic from an instance is expected.
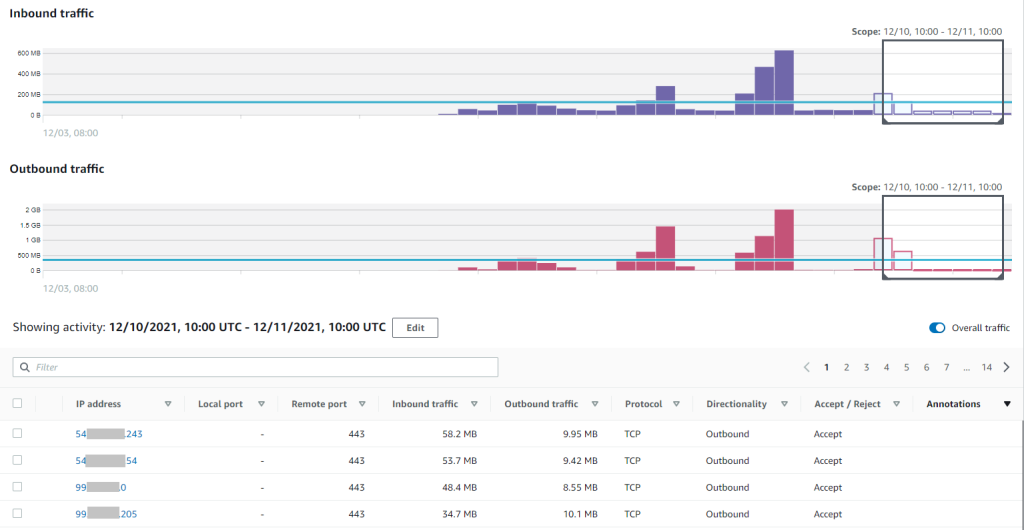
If you click to some EC2 instance, you will see details about incoming/outgoing traffic, IP addresses, ports, protocols, etc.
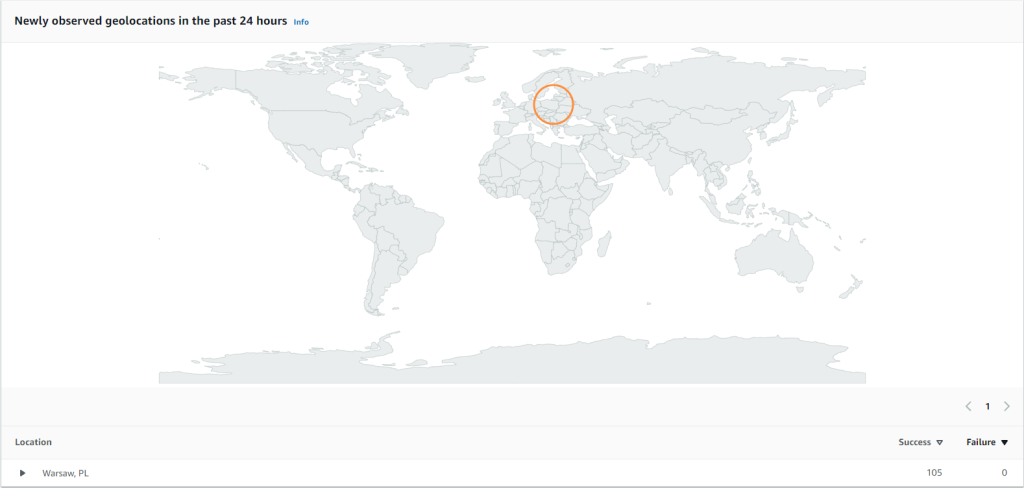
The third summary tab is “Newly observed geolocations in the past 24 hours”
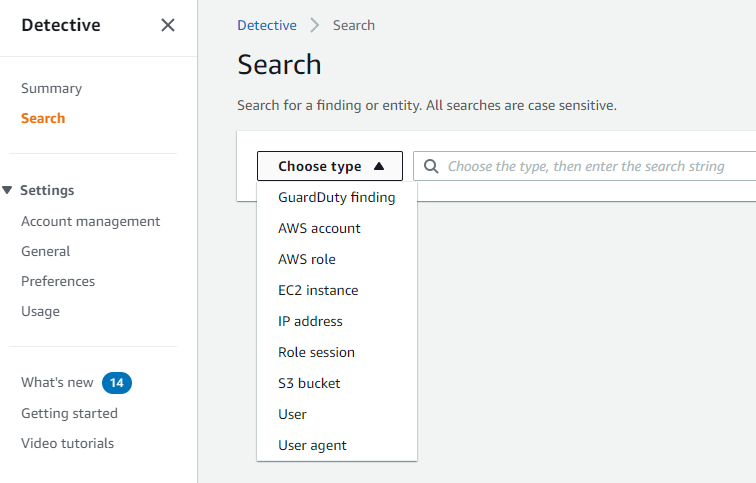
Amazon Detective also provides a search capabilities, which you can use in the investigation process:
Amazon Detective is priced based on the volume of data ingested from AWS CloudTrail, VPC Flow Logs, and Amazon GuardDuty findings. You are charged Per Gigabyte (GB) ingested per account/region/month. There is no additional charge to enable these log sources for analysis or for data stored in Amazon Detective.
You can try Amazon Detective at no additional charge with a 30-day free trial. The free trial enables you to get the full Detective feature set over the 30-day period. After the free trial it will cost $2.00 per GB for the first 1,000 GB/account/region/month.
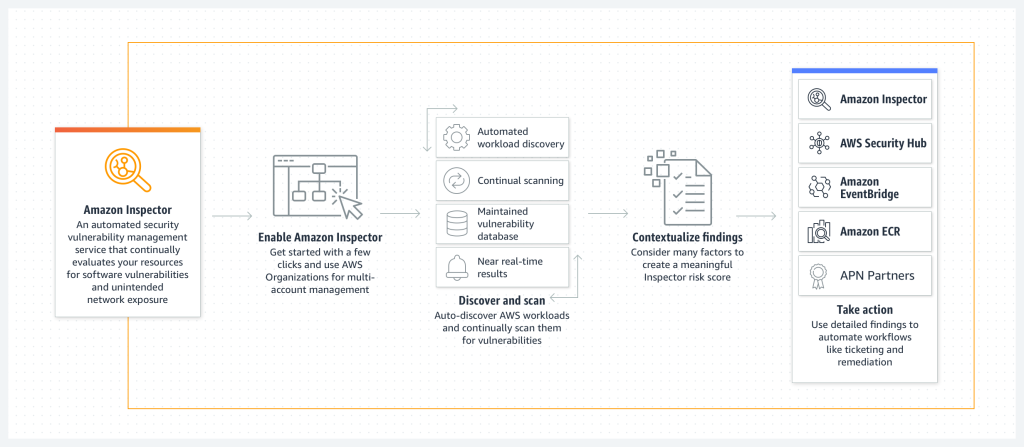
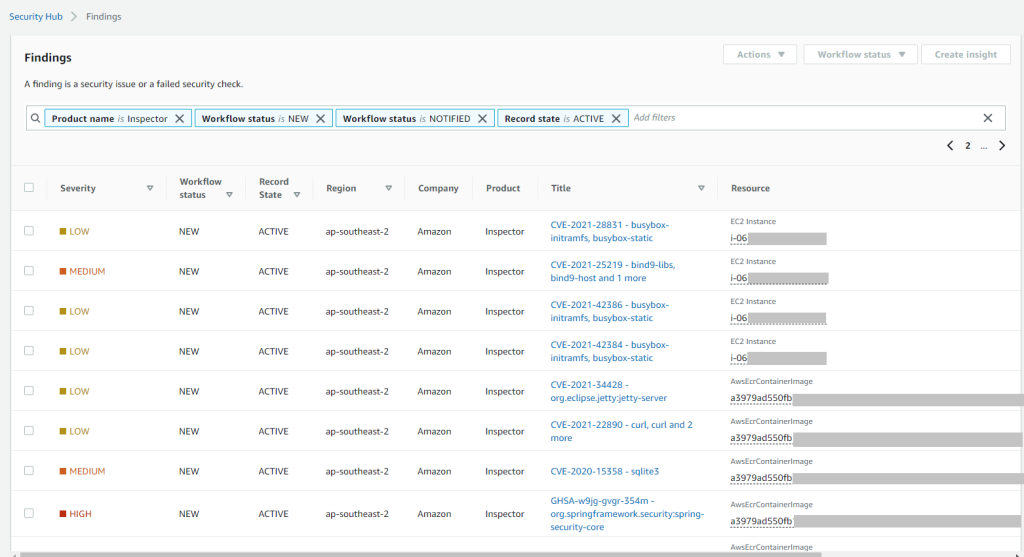
Amazon Inspector integration
Amazon Inspector is an automated vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure. It allows us to discover vulnerabilities quickly, prioritize patch remediation, meet compliance requirements and identify zero-day vulnerabilities sooner.
EC2 requires the Inspector agent for performing scans, ECR repos don’t need any additional configuration for scanning.
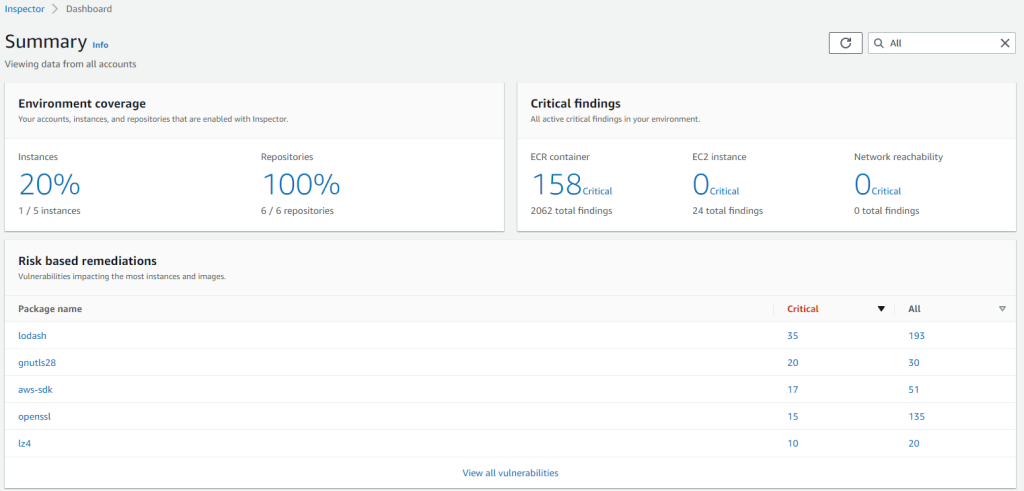
Amazon Inspector Summary dashboard shows the following. Number of covered EC2 instances and ECR repositories, number of critical findings and packages with vulnerabilities.
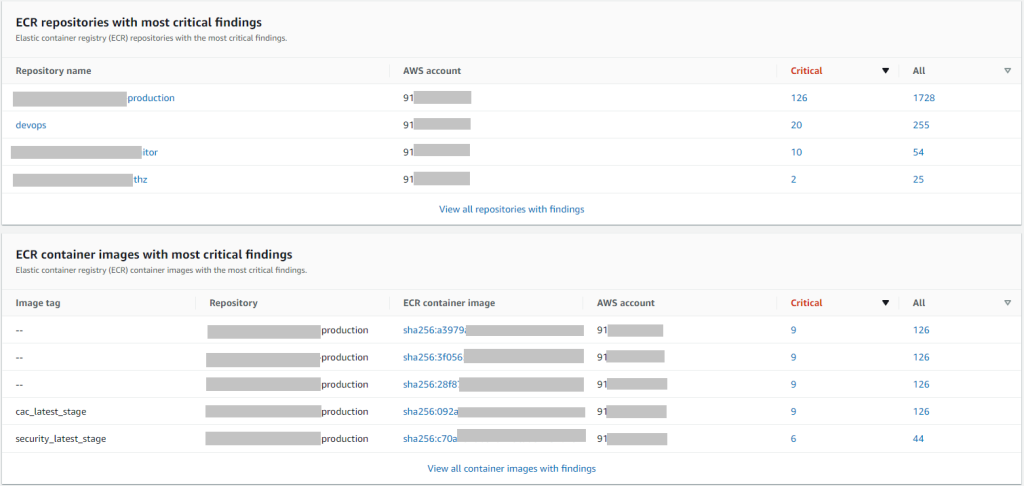
ECR repositories and container images with most critical findings.
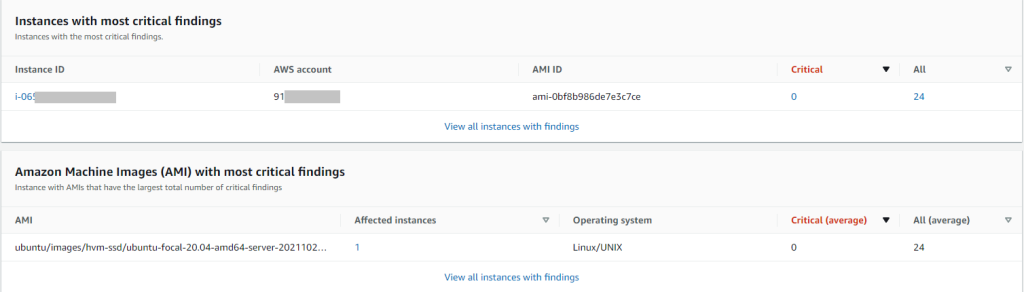
EC2 instances and AMIs with most critical findings.
Once you enable Amazon Inspector and AWS Security Hub, findings are automatically delivered to the Security Hub console.
All accounts new to Amazon Inspector are eligible for a 15-day free trial to evaluate the service and estimate its cost. During the trial, all eligible Amazon Elastic Compute Cloud (EC2) instances and container images pushed to Amazon Elastic Container Registry (ECR) are continually scanned at no cost. Additionally, you can review estimated spend in the Amazon Inspector console, including aggregated organization-wide spend in the central Amazon Inspector administrator account. This way, you can understand and estimate the cost of using Amazon Inspector for automated and continual vulnerability scans across Amazon EC2 and ECR for your entire organization before deciding.
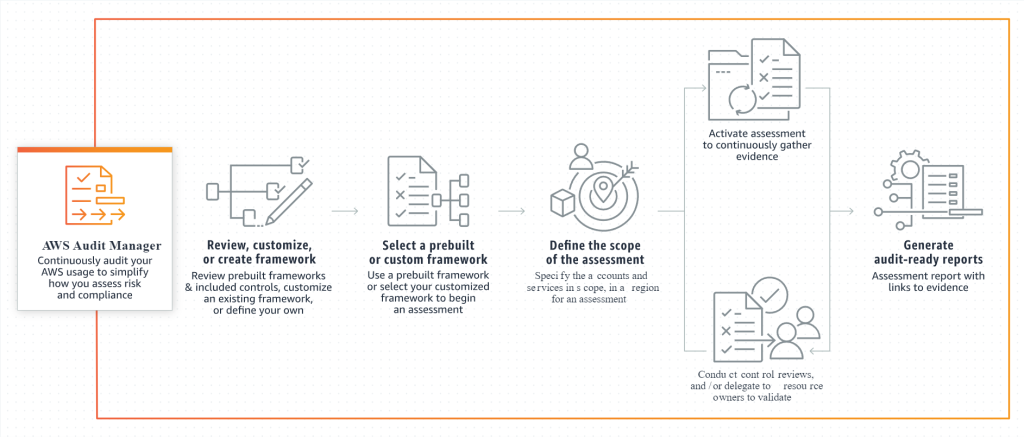
AWS Audit Manager integration
AWS Audit Manager helps you continuously audit your AWS usage to simplify how you assess risk and compliance with regulations and industry standards.
With Audit Manager you can easily map your AWS usage to control, save time with automated collection of evidence and always be prepared to produce audit-ready reports.
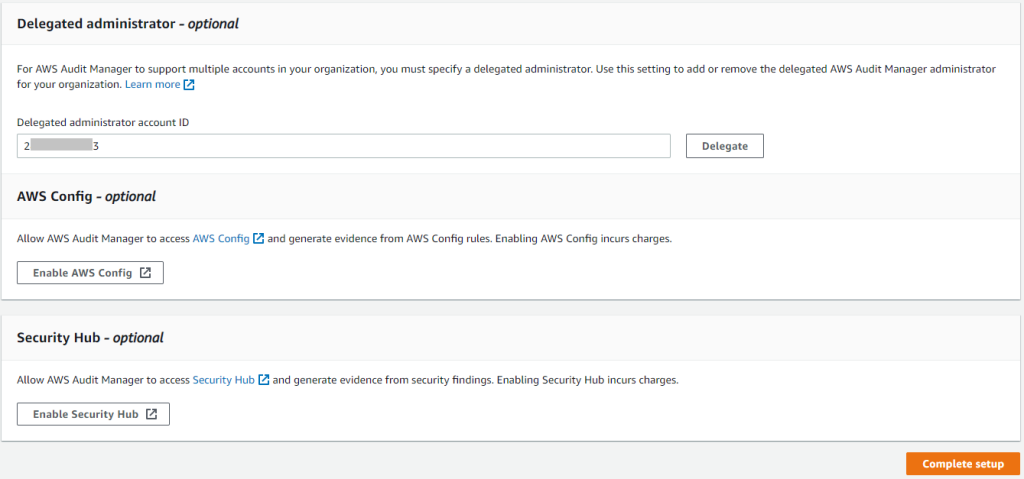
For automated evidence collection AWS Audit Manager needs AWS Config and AWS Security Hub. As in other AWS security services you can set a delegated administrator. In our case this is again the “Audit” account.
There are 22 standard frameworks in the AWS Audit Manager library and you can also create custom ones.
| Framework name | Compliance type | Control sets | Controls |
|---|---|---|---|
| AWS Audit Manager Sample Framework | AWS Audit Manager Sample Framework | 3 | 5 |
| AWS Control Tower Guardrails | AWS Control Tower Guardrails | 5 | 14 |
| AWS Foundational Security Best Practices | AWS Foundational Security Best Practices | 29 | 121 |
| AWS License Manager | AWS License Manager | 6 | 27 |
| AWS Operational Best Practices | AWS Operational Best Practices | 20 | 52 |
| AWS Well Architected Framework | AWS Well Architected Framework | 2 | 16 |
| CIS Benchmark for CIS Amazon Web Services Foundations Benchmark, v1.2.0, Level 1 | CIS | 4 | 36 |
| CIS Benchmark for CIS Amazon Web Services Foundations Benchmark, v1.2.0, Level 1 and 2 | CIS | 4 | 49 |
| CIS Benchmark for CIS Amazon Web Services Foundations Benchmark, v1.3.0, Level 1 | CIS | 6 | 38 |
| CIS Benchmark for CIS Amazon Web Services Foundations Benchmark, v1.3.0, Level 1 and 2 | CIS | 6 | 55 |
| CIS Controls v7.1 IG1 | CIS Controls | 16 | 43 |
| FedRAMP Moderate Baseline by Allgress | FedRAMP | 325 | 1211 |
| GDPR | GDPR | 10 | 371 |
| Gramm-Leach-Bliley Act (GLBA) | Gramm-Leach-Bliley Act (GLBA) | 16 | 114 |
| GxP 21 CFR Part 11 | GxP 21 CFR Part 11 | 7 | 27 |
| GxP EU Annex 11 | GxP EU Annex 11 | 3 | 32 |
| HIPAA | HIPAA | 6 | 88 |
| NIST 800-53 (Rev. 5) Low-Moderate-High | NIST | 280 | 1007 |
| NIST Cybersecurity Framework version 1.1 | NIST | 23 | 108 |
| NIST SP 800-171 Rev. 2 | NIST | 16 | 124 |
| PCI DSS V3.2.1 | PCI DSS | 12 | 662 |
| SOC 2 | SOC 2 | 20 | 61 |
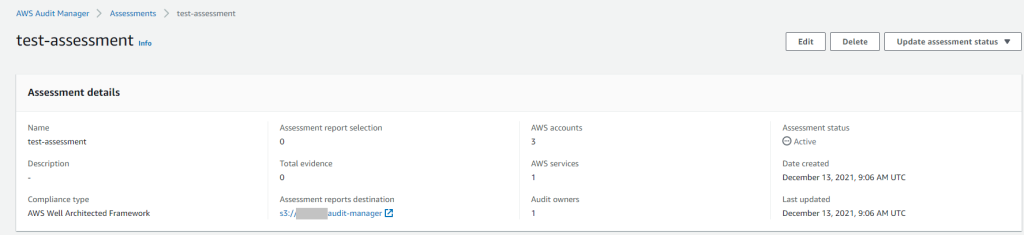
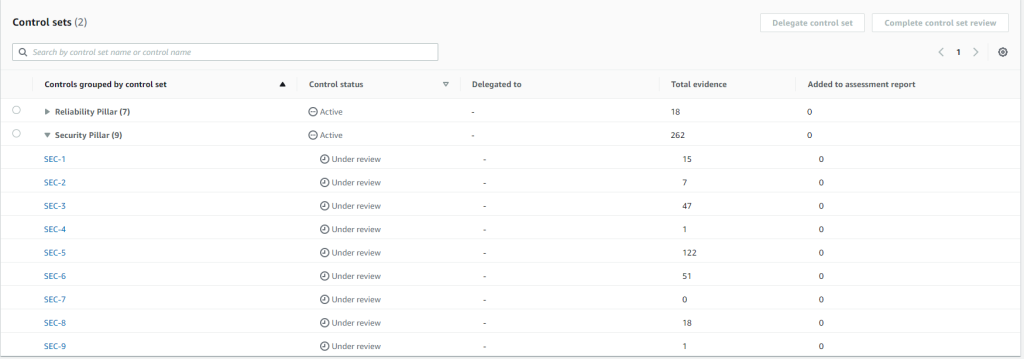
For starting assessment you need to select a framework, S3 bucket for a generated report and select AWS accounts which you need to assess. In the following example we are checking AWS Well Architected Framework for 3 accounts.
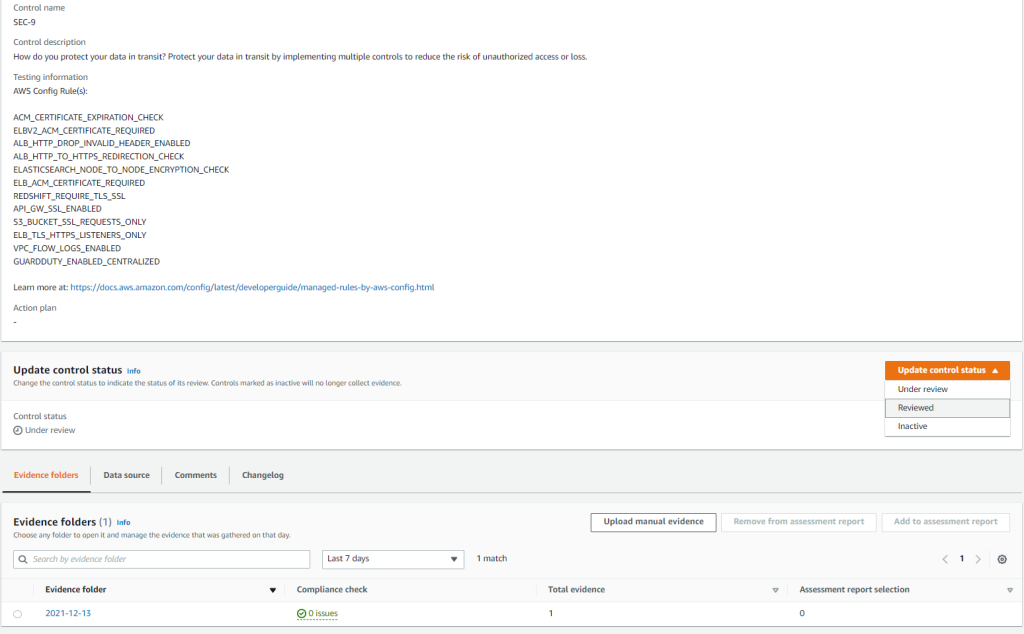
Once all evidence is collected, you need to review every control.
In every control you can set status “Reviewed”, “Inactive” or leave it “Under review”.
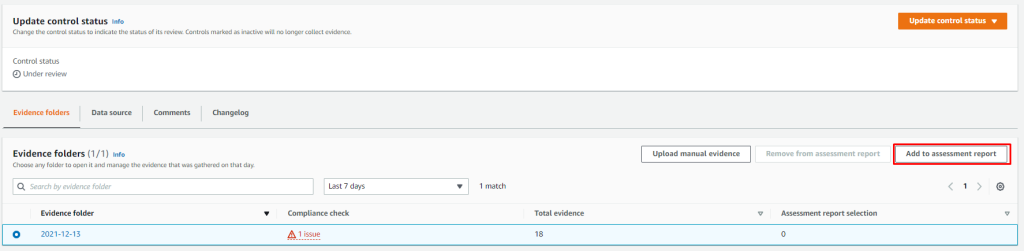
Or you can add evidence to report.
Once everything is reviewed you can generate a report.
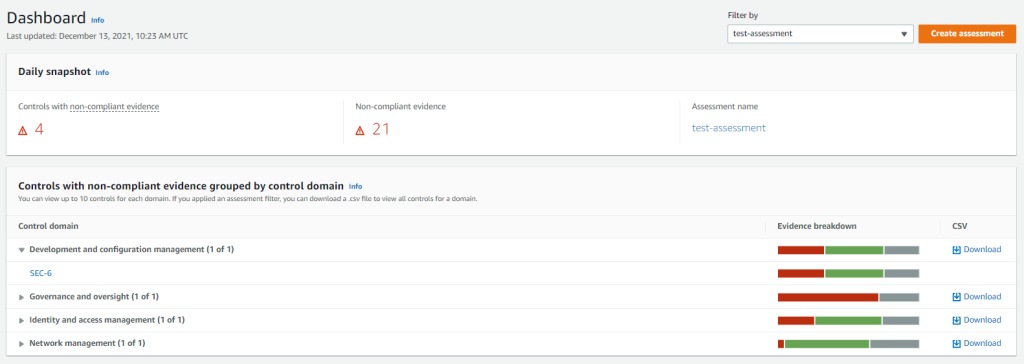
In the AWS Audit Manager dashboard you can see a summary for different controls and evidence.
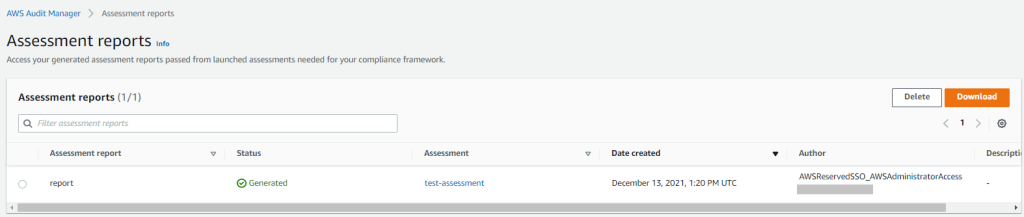
Once the report is generated you can download an archive containing a report summary, every evidence summary and digest file for integrity checks.
AWS Audit Manager offers a free tier for first-time customers. The free tier will expire in two calendar months after the first subscription. The free tier offers 35,000 AWS Audit Manager resource assessments per month for two calendar months. After that it will cost $1.25 per 1,000 Audit Manager resource assessments per account per region.
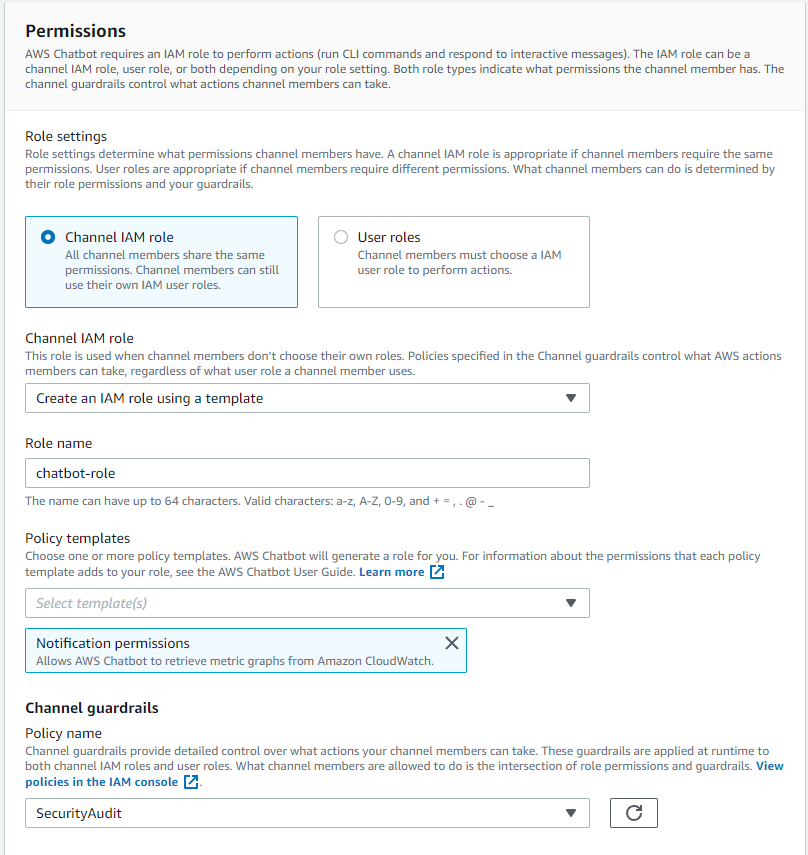
AWS Chatbot integration
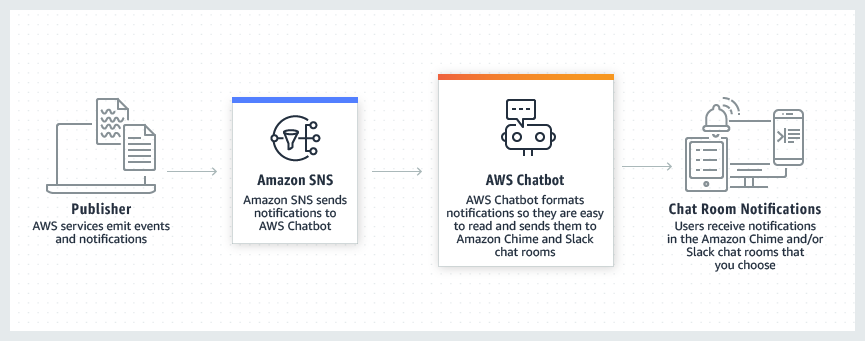
AWS Chatbot is an interactive agent that makes it easy to monitor, operate, and troubleshoot your AWS workloads in your chat channels. With AWS Chatbot, you can receive alerts, run commands to retrieve diagnostic information, configure AWS resources, and initiate workflows.
In the following example we configure Slack notifications for the AWS Security Hub findings. First of all you need to authorize AWS Chatbot in your Slack workspace and configure the client.
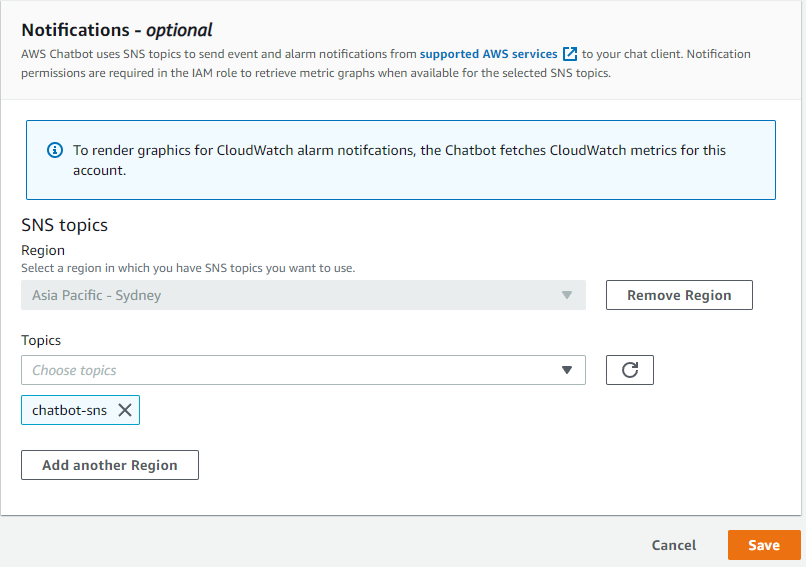
You also need to create an SNS topic which will be receiving events from CloudWatch and forward them to AWS Chatbot via https subscription.
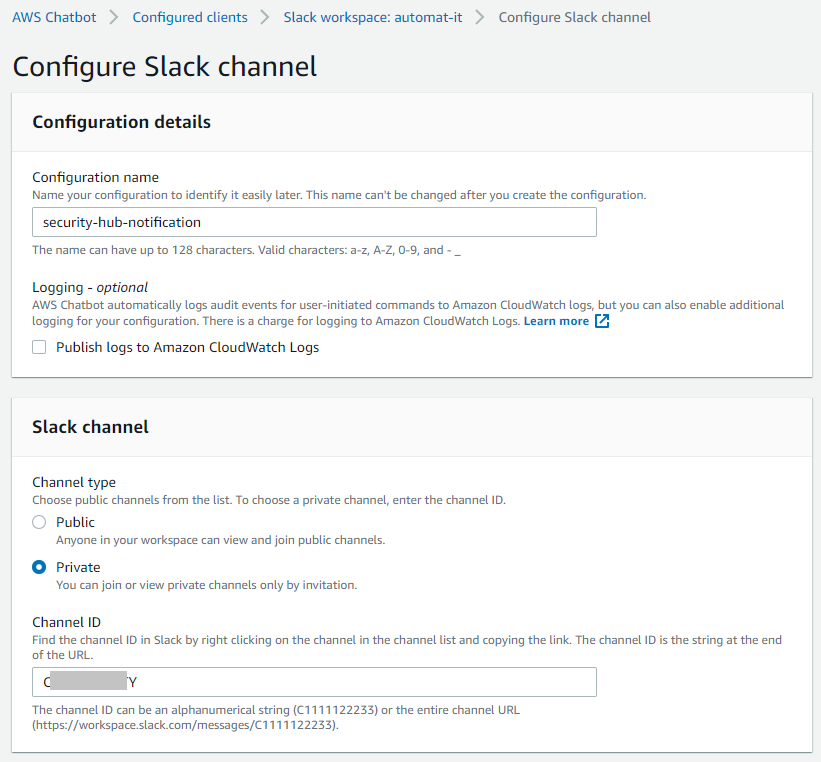
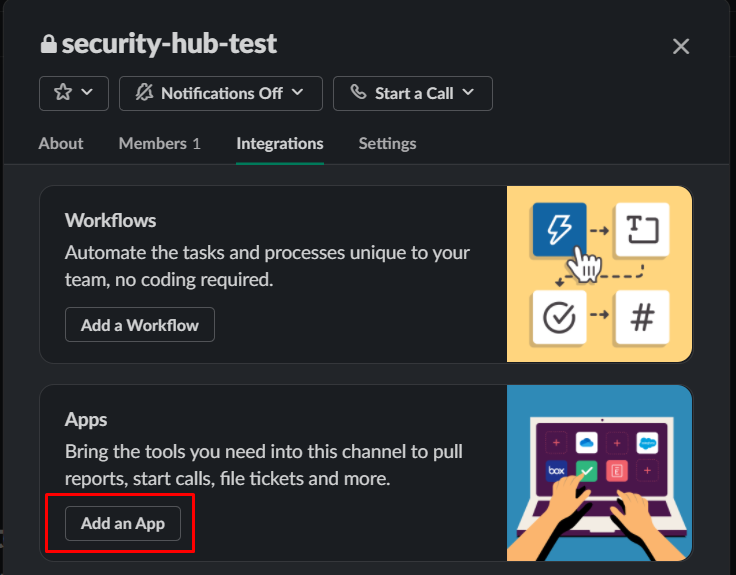
And finally you need to add an AWS Chatbot application to your Slack workspace.
The following Event Bridge rule can be used for sending notifications to the created earlier SNS topic.
{
"detail-type": ["Security Hub Findings - Imported"],
"source": ["aws.securityhub"],
"detail": {
"findings": {
"Severity": {
"Label": [
"HIGH",
"CRITICAL"
]
}
}
}
}
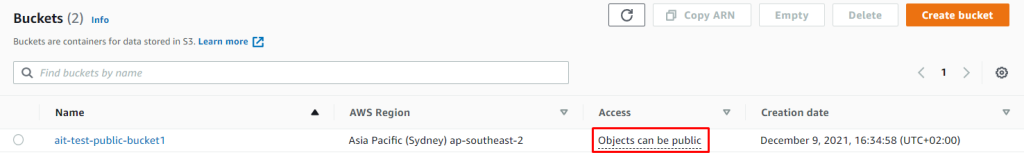
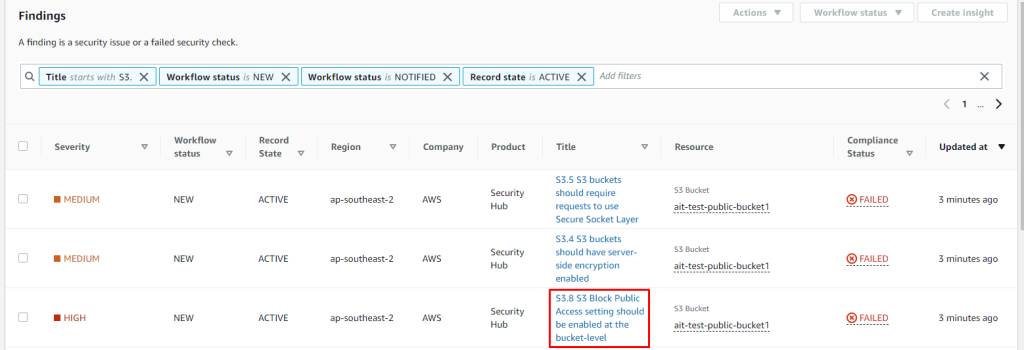
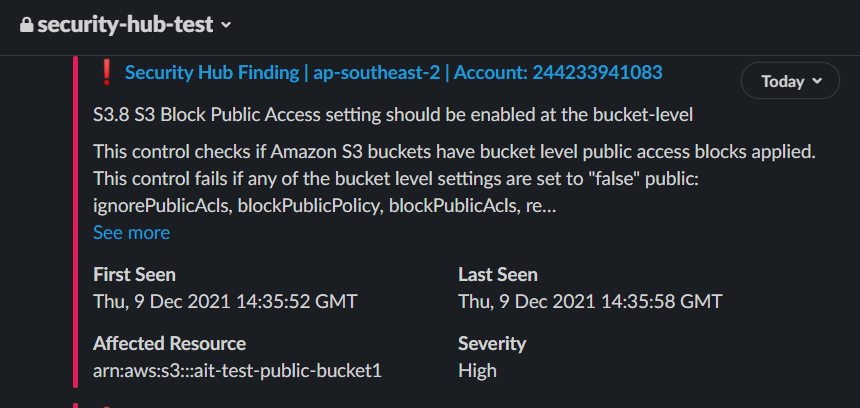
As a test we can create an S3 bucket that is not blocking public access and Amazon Macie will notice it.
And we immediately receive Slack notification.
There is no additional charge for AWS Chatbot. You pay only for the underlying services (such as Amazon Simple Notification Service, Amazon CloudWatch, Amazon GuardDuty, and AWS Security Hub) that you use, in the same manner as if you were using them without AWS Chatbot. Additionally, there are no minimum fees and no upfront commitments.
Conclusion
AWS Security Hub has a lot of possible integrations. In this post we have covered 7 AWS services. You can also configure integration with other AWS services as AWS Firewall Manager, AWS Systems Manager OpsCenter, AWS Systems Manager Patch Manager and 60 third-party integrations developed by Aqua Security, Atlassian, IBM, McAfee, Palo Alto Networks, Pagerduty, Rapid7, Sumo Logic, Symantec and others. AWS Security Hub and other AWS security related services work well in multi-account deployment and can help us easier review and react to different issues. Automat-IT conducts Well Architected Review including Security Pillar, uses mentioned services and suggests to its customers to do likewise.